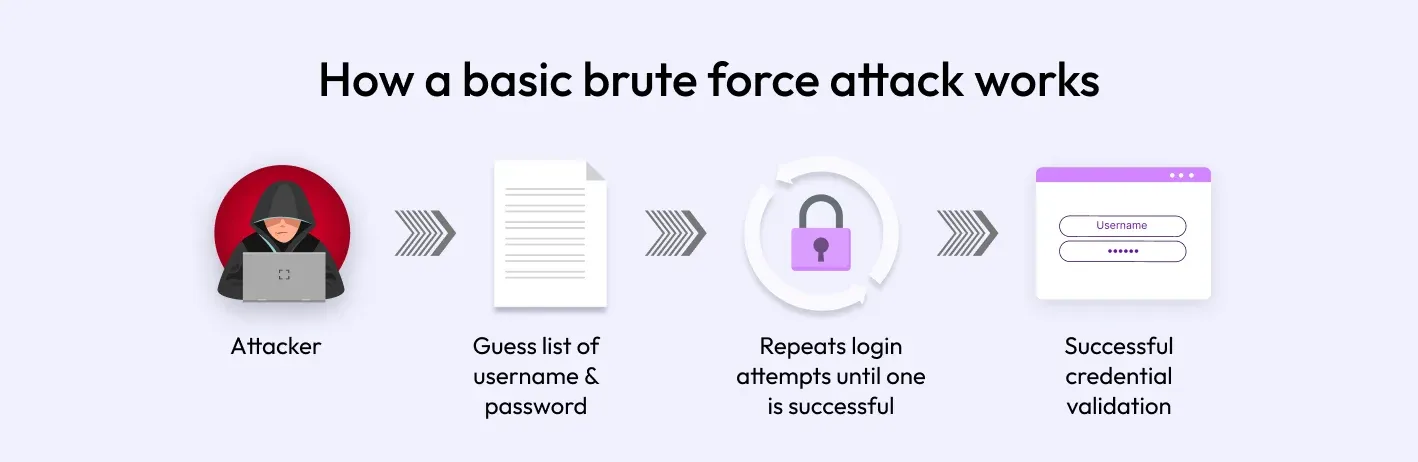
Have you ever thought about how hackers can break into your online accounts and access your passwords? A brute force attack is a common and effective method used for hacking. The term "brute force attack" might sound scary in the realm of cybersecurity, and for good reason. Hackers use this technique to crack passwords and gain unauthorized access. So, what exactly is a brute force attack?
Imagine a burglar attempting to open a locked door by trying every possible combination of keys until they find the right one. A brute force attack operates on a similar principle in the digital world. It tries every possible combination of characters until it discovers the correct password. This trial-and-error approach relies on the sheer volume of attempts rather than any specialized knowledge or skill. Keep reading to learn everything about the brute force attack and prevention strategies.
Let's delve into what a brute force attack is, the different types of brute force attacks, why brute force attacks occur, how to prevent brute force attacks, and the best brute force attack tools for penetration testing.